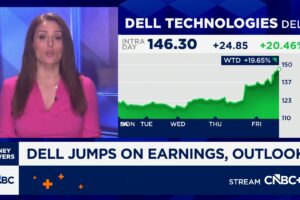
The type of personal information compromised in thefts like Capital One’s COF, -1.16% data hack could hold the “keys to the kingdom” for a bad actor, experts say — and she or he can do far more than open a credit card in your name.
The company revealed Monday night that it had learned of a hack impacting about 100 million U.S. customers and 6 million people in Canada. Authorities charged 33-year-old software engineer Paige Thompson, a former Amazon Web Services AMZN, -1.73% employee, with one count of computer fraud and abuse, an offense that carries up to five years in prison.
Though Capital One stressed in a statement that “no credit-card account numbers or log-in credentials were compromised and over 99% of Social Security numbers were not compromised,” it conceded that some 140,000 Social Security numbers and 80,000 linked bank-account numbers had indeed been compromised. Other compromised information included names, dates of birth, self-reported income, addresses, zip codes, email addresses and phone numbers, the company said.
‘The Social Security number basically is a password.’
“Based on our analysis to date, we believe it is unlikely that the information was used for fraud or disseminated by this individual,” Capital One said. “However, we will continue to investigate.” The company said it would notify impacted customers “through a variety of channels” and provide them with free identity protection and credit monitoring.
The Social Security numbers from credit-card applications had been “tokenized or encrypted,” according to a Justice Department complaint, while information like names, dates of birth, addresses and credit-history information had not. But security experts warn that in general, Social Security numbers and other personal details can be exploited for purposes well beyond taking out a line of credit — including medical, employment and criminal identity theft.
“That [Social Security number] is connected to so many credit-driven and governmental services, and what most people don’t realize is that the Social Security number basically is a password,” Robert Siciliano, a security and privacy expert at the online security resource Safr.Me, told MarketWatch. “It shouldn’t be that easy, but that’s what our credit system, banks, lenders, retailers and our government has designed — and they didn’t really think that one through.”
An enterprising identity thief might pose as you using your Social Security number to get a job.
Plus, “combined with other major breaches, like Equifax EFX, -0.09% , the SSNs can still be used to steal identities when correlated with other personally identifying data in those other public data dumps,” said Katie Moussouris, the founder and CEO of Luta Security.
In the wake of a large data breach like this one, consumers should check if their accounts have been affected, sign up for additional fraud protection and understand the difference between a credit freeze and a credit lock. But they should also consider several other ways in which a bad actor could exploit their personal data.
Here are five more worst-case scenarios to watch out for — and how best to protect yourself:
An imposter gets a job under your name. An enterprising identity thief might pose as you using your Social Security number (along with an easily obtainable fake ID) to get a job, Siciliano said. The imposter’s wages could then be reported in your name, sticking you with an Internal Revenue Service tax bill you shouldn’t owe.
While there isn’t much you can do to prevent this from happening, identity-theft and privacy expert Carrie Kerskie said, you can freeze your Social Security number in E-Verify, the government tool used by some employers to verify employment eligibility.
An imposter using your name and personal identity to access health care can be costly to resolve and potentially dangerous to your health.
E-Verify lets users “Self Lock” their Social Security number and unlock it whenever a new employer needs to vet them. “If your locked SSN is entered in E-Verify to confirm employment authorization, it will result in an E-Verify mismatch, called a tentative non-confirmation,” E-Verify’s site says. “By using Self Lock, you can block someone from committing this fraud if they gain employment with an E-Verify employer.” But “this isn’t 100%,” Kerskie said, as not every employer uses this system.
Someone claims your Social Security benefits or files taxes under your name. Though this reportedly isn’t a foolproof approach, you should create a MySSA account with the Social Security Administration, Kerskie said. “If you don’t set it up, you leave it wide open for a bad guy to do it on your behalf,” she said. “So by setting it up, you’re marking your territory.” Anyone over age 18 with the required information can create an online account.
As for fraud related to tax returns, you may be eligible to use an IRS Identity Protection PIN (IP PIN) — which bars another person from filing tax returns using your Social Security Number — on your federal income tax returns. Eligible parties will have received a CP01A notice from the IRS; received a letter from the IRS inviting them to get an IP PIN; or filed their federal return last year as a California, Delaware, Florida, Georgia, Illinois, Maryland, Michigan, Nevada, Rhode Island or Washington, D.C. resident.
In some cases, like if the IRS rejects your tax return because someone has already filed a return using your Social Security number, you may be able to fill out an identity-theft affidavit (Form 14039).
Someone uses your identity to obtain medical services or prescription drugs. An imposter’s using your name and personal identity to access health care can be costly to resolve and potentially dangerous to your health. After all, Kerskie said, this person’s test results and symptoms could wind up on your medical record. “When you go to the doctor and they’re trying to make a diagnosis, are they looking at only your symptoms and your test results, or are they commingled with your imposter’s?” Kerskie said. “There have been situations where it’s led to misdiagnosis.”
A bad actor gaining access to your calls and text messages also spells bad news for two-factor authentication that uses SMS codes.
Your best defense against medical identity theft is monitoring, Kerskie said. Scrutinize any explanation of benefits you receive from your insurance company, noting dates, names of providers and summaries of services rendered, she said, calling your insurance company to report any discrepancies. Ask your health-care provider for a copy of your medical file, Kerskie added, and speak up if a provider mentions any medications or tests you haven’t received. “You can’t err on the side of caution,” she said. “You have to ask questions.”
A thief hijacks your cell phone — and is now receiving all of your calls and texts. They can achieve this by transferring your phone account to another carrier, Kerskie said, or by using your personal information to call your carrier and switch your SIM card to a new device. And while many mobile carriers allow customers to create a PIN or passcode as an extra layer of security beyond their name, address, date of birth and Social Security number, Kerskie says many people lean on lazy, easy-to-guess passwords using their birthday or the last four digits of their Social.
A bad actor gaining access to your calls and text messages also spells bad news for two-factor authentication that uses SMS codes. “The bad guys know this — so once they steal your number, they will go to major financial institutions and they will initiate a password reset for your account,” Kerskie said.
As data breaches are only likely to grow more common, you should protect yourself using multi-factor authentication through an app like Google Authenticator GOOG, -1.24% GOOGL, -1.28% or Microsoft Authenticator MSFT, -0.84%, Moussouris said. For additional protection, you could go with a hardware-based security token, she added.
Someone steals your identity and gets charged with a crime. This could negatively impact your own job prospects if you have a criminal record you’re unaware of, Kerskie said, or even affect your car-insurance rates if someone is racking up traffic violations in your name.
Try requesting your criminal background check from your county, your state or some other database, she suggested, or request an Identity History Summary from the FBI. Google your name every now and then to see what turns up, she added. “If there’s anything that seems off,” she said, “you need to take some extra time and some extra steps to look into it.”